Projects / Articles
Some of my recent projects.

Some of my recent projects.

Sometimes, especially in long-term projects, it is common for the URLs we use in development or test environments to leak to clients, users, or even malicious people.
A very simple way to protect work environments is to use Azure Active Directory; Especially if your project is with Azure, it is common for you to have its collaborators registered as users in the active directory of the subscription.
This small example shows how Web Applications are protected within Azure Using the same active directory
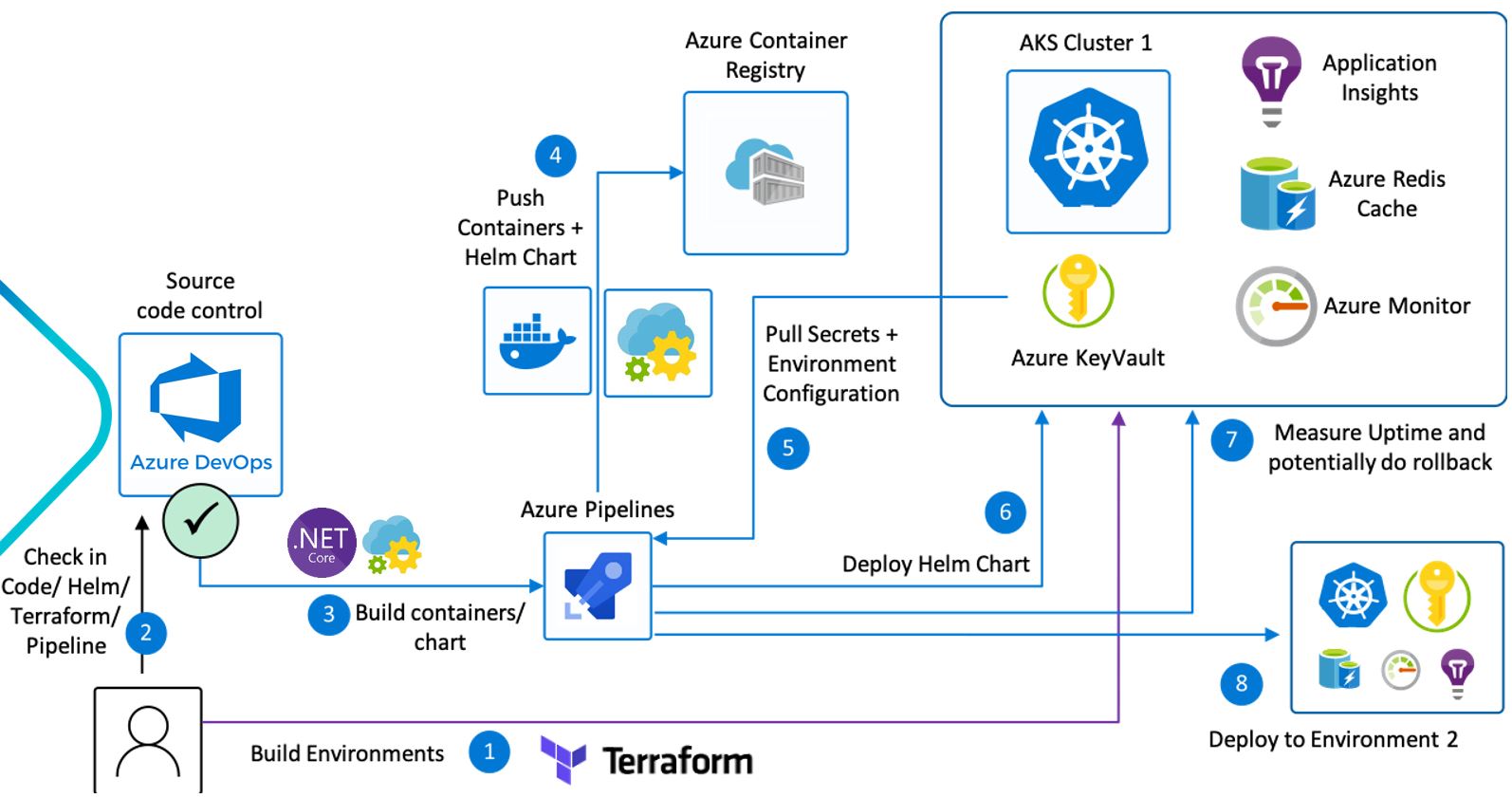

We will deploy application in Dotnet Core 3.1 in Docker Containers to Container Registry in Azure, creating a Kubernetes Cluster with Terraform and Helm for internal routing and management of open authority certificates with integration with our own domain and continued delivery in Microsoft DevOps.
View

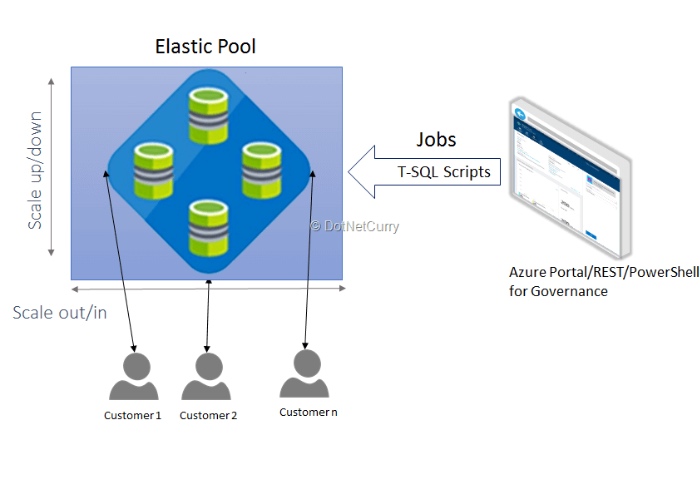
Create Continuous integration of DACPACs for SQL Azure Elastic Pools!
View
And example of how to use docker as Azure Function with a queue service.
View
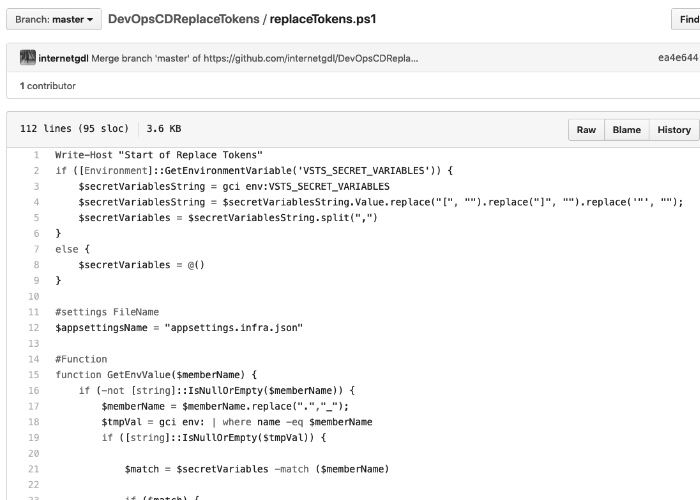
Replace tokens in appsettings.json file with Powershell integrating as step of the release pipeline.
View